TCP/IP’s Layered Architecture (p208)
- When a set of protocols works cooperatively, it’s called a protocol stack or protocol suite.
- The most common protocol stack is Transmission Control Protocol/Internet Protocol (TCP/IP), the Internet protocol suite.
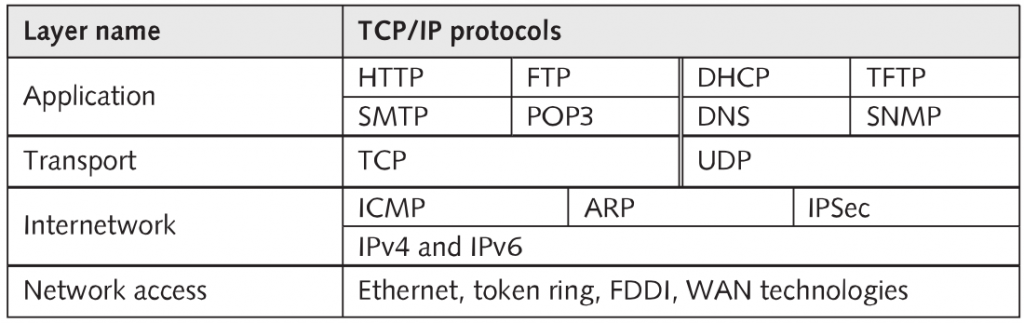
Role of Network Access Layer (p213)
- Provides a physical (MAC) address for the network interface.
- Verifies that incoming frames have the correct destination MAC address.
- Defines and follows media access rules.
- Receives packets from the Internetwork layer and encapsulates them to create frames.
- Did encapsulates received frames and send the resulting packets to the Internetwork layer.
- Often provides friend Eric Jackson in the form of a CRC code.
- Transmits and receives bit signals.
- Defines the signaling needed to transmit bits, whether electrical, light pulses, or radio waves.
- Defines the media and connectors needed to make a physical network connection.
Role of the Internetwork Layer (p213)
- Defines and verifies IP addresses.
- Routes packets through an Internetwork.
- Results MAC addresses from IP addresses.
- Delivers packets efficiently.
Defines & Verfies IP Addresses
- IP addresses are use for two main purposes
- to identify a network device at the Internetwork layer
- to identify the network on which the device resigns.
- When a Host receives an IP packet, it compares the package destination at IP address with its own address to verify that the package has delivered correctly.
- If the destination address matches or is a broadcast, the packet is processed.
- network ID: in a class B this is the first 2 octets – xxx.xxx.1.101
- host ID: in a class B this is the last 2 octets – 172.16.xxx.xxx
Routes Packets Through an Internetwork
- Determining the best way to get a packet from network to network until it reaches its destination.
Resolves MAC Addresses
- ARP: Address Resolution Protocol.
- Returns a computer’s MAC address by asking the network which computers assigned a particular IP address.
Delivers Packets Efficiently
- The secret to efficiency is low processing overhead.
- Protocols in the Transport and Application layers provide advanced reliability features.
- Protocols at this layer are concerned with one packet at a time, with no concern for packets that came before or after it and with no confirmation that delivery was successful. This communication strategy is called connectionless communication and protocols using it are called connectionless protocols.
Protocols at the Internetwork Layer (p215)
- IPv4: Internet Protocol version 4
- IPv6: Internet Protocol version 6
- ARP: Address Resolution Protocol
Role of the Transport Layer (p222)
- The Transport layer provides reliability to the Internet
- TCP: connection oriented and designed for reliable transfer of information in complex internetworks.
- Working with Segments: For outgoing data, in which the Application-layer protocol requires the services of the Transport-layer protocol, the Application layer passes data to TCP or UDP, depending on which protocol it was designed to use. Both TCP and UDP add a header is added to the data to make it a segment. The Transport-layer protocol then passes the segment to the internetwork-layer protocol, usually IP. With incoming data, the internetwork layer protocol didn’t calculate the packet and forward the resulting segment to the Transport-layer protocol.
- TCP and UDP use Port numbers to specify the source and destination Application-layer protocols.
- Protecting Data / checksum
- Unlike the CRC that can be recalculated along the way, the checksum cannot.
- Intermediate devices don’t recalculate the checksum in the Transport layer, so if data corruption occurs along the way, the final receiving station detects the checksum error and discards the data.
TCP: The Reliable Transport Layer
- general info
- 3 way handshake: SYN, SYN-ACK or RST, ACK
- segmenting data:
- Ethernet can only send frames that are a maximum of 1518 bytes.
- It’s TCP’s job to break the data into smaller segments before handing each segment to the Internetwork layer.
- Each segment is labeled with a sequence number so they can be reassembled in order.
- flow control: prevents a destination from becoming overwhelmed by data, resulting in dropped packets.
Role of Application Layer (p225)
- Provides network services to user applications that access network resources.
- HTTP: HyperText Transfer Protocol – Port 80
- POP3: Post Office Protocol version 3 – TCP port 110
- IMAP: Internet Message Access Protocol – TCP port 143
- SMTP: Simple Mail Transfer Protocol – TCP port 25
- DHCP: Dynamic Host Configuration Protocol – UDP
- DNS: Domain Name System – name to address resolution protocol
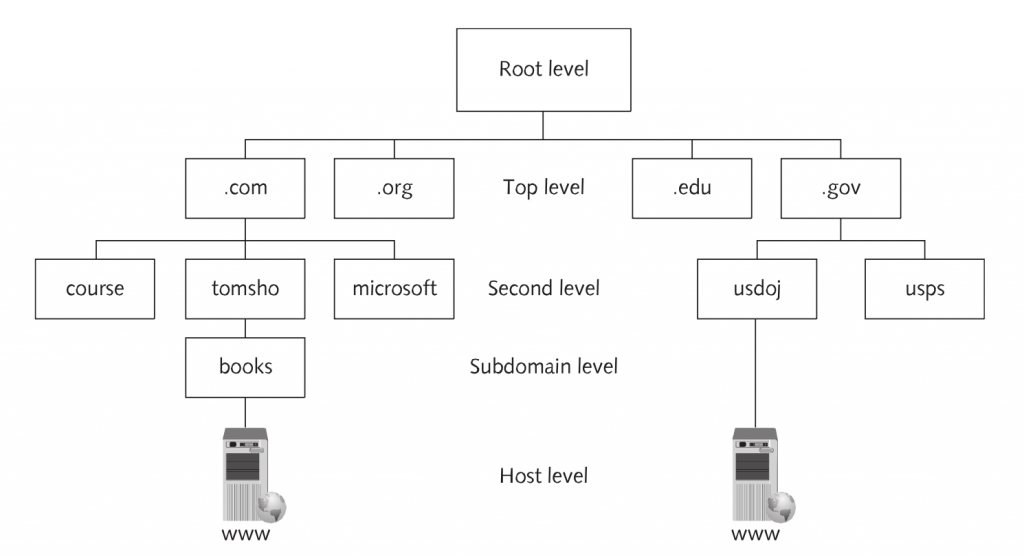
IP Addressing (p232)
- Responsible for addressing and routing in the TCP/IP environment.
IP address classes
| Class | 1st Octet Decimal Range | 1st Octet High Order Bits | Network/Host ID (N=Network, H=Host) | Default Subnet Mask | Number of Networks | Hosts per Network (Usable Addresses) |
|---|---|---|---|---|---|---|
| A | 1 – 126* | 0 | N.H.H.H | 255.0.0.0 | 126 (27 – 2) | 16,777,214 (224 – 2) |
| B | 128 – 191 | 10 | N.N.H.H | 255.255.0.0 | 16,382 (214 – 2) | 65,534 (216 – 2) |
| C | 192 – 223 | 110 | N.N.N.H | 255.255.255.0 | 2,097,150 (221 – 2) | 254 (28 – 2) |
| D | 224 – 239 | 1110 | Reserved for Multicasting | |||
| E | 240 – 254 | 1111 | Experimental; used for research | |||
Note: Class A addresses 127.0.0.0 to 127.255.255.255 cannot be used and is reserved for loopback and diagnostic functions.
Private IP Addresses
| Class | Private Networks | Subnet Mask | Address Range |
|---|---|---|---|
| A | 10.0.0.0 | 255.0.0.0 | 10.0.0.0 – 10.255.255.255 |
| B | 172.16.0.0 – 172.31.0.0 | 255.240.0.0 | 172.16.0.0 – 172.31.255.255 |
| C | 192.168.0.0 | 255.255.0.0 | 192.168.0.0 – 192.168.255.255 |
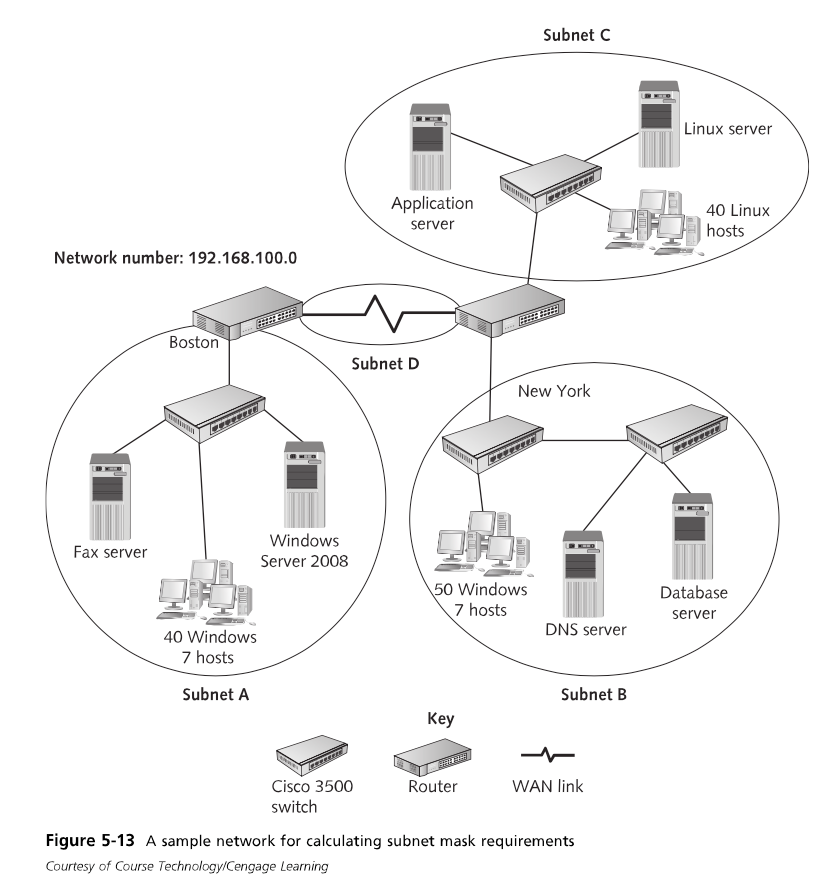
Why Subnet (p239)
- Makes more efficient use of available IP addresses.
- With subletting, a company can divide its network into logical groups. When one large network is divided into two or more smaller subnetworks, a router is needed to allow hosts on one subnetwork to communicate with hosts on another subnetwork.
- Subnetting can make network communication more efficient. Because routers don’t forward broadcast traffic from one subnet to another, broadcast traffic generated by one subnet of 125 computers is heard and processed only by those 125 computers.
- If you have a single network of 500 computers, the amount of broadcast traffic is often detrimental to overall network performance.
Calculating a Subnet (p243)
- Decide how many subnets you need.
- Decide how many bits you need to meet or exceed the number of required subnets. This value is calculated by the formula 2ⁿ, with n representing the number of bits you must reallocate from the host ID to the network ID.
IPv6 (p248)
- general info (not available on course web for some reason)